Building Smarter Branches: The Deployment Choices That Matter
Why Deployment Choices Matter The branch is no longer a remote outpost; it's where customer experience, cloud... more
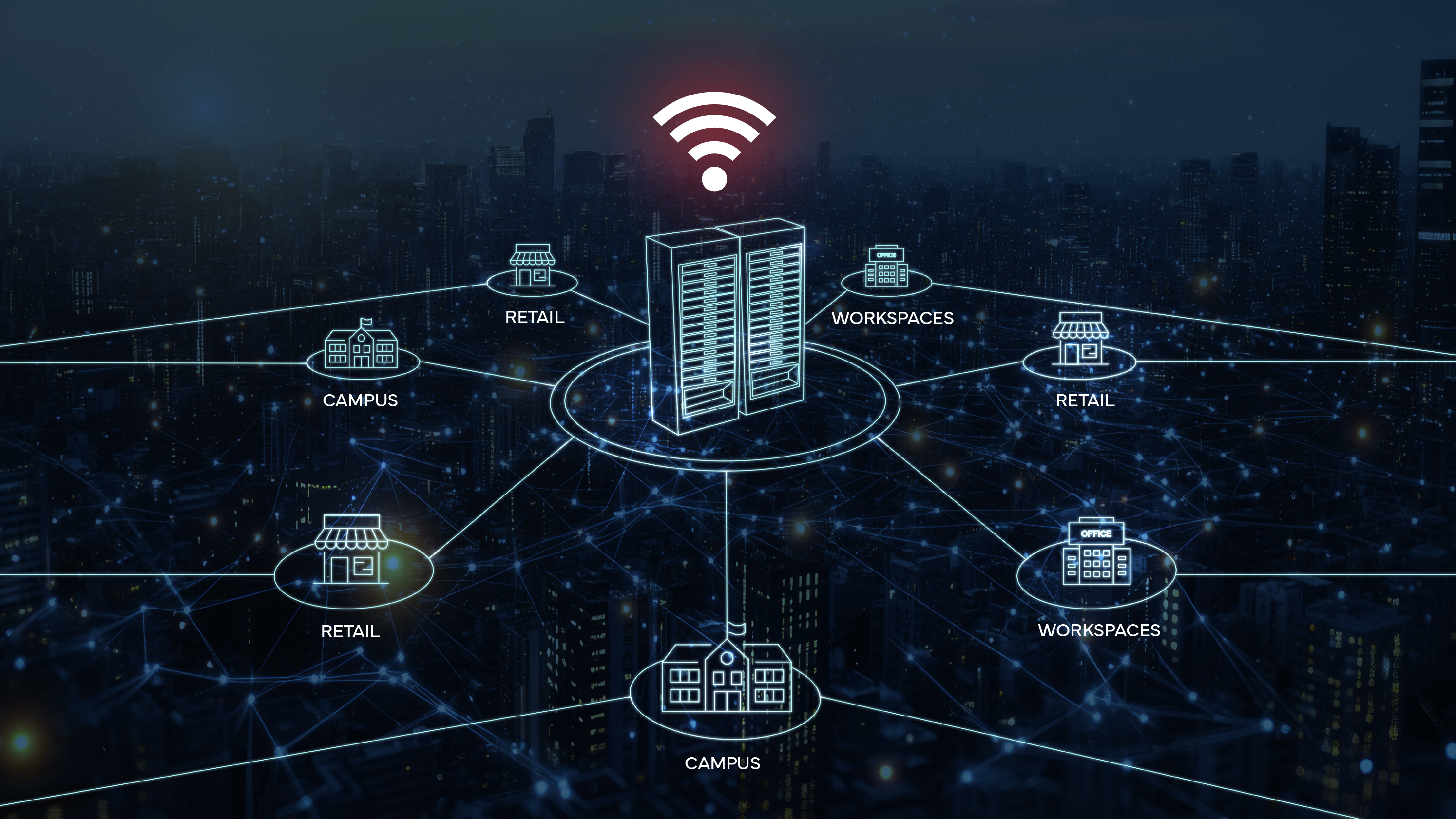
Why Deployment Choices Matter The branch is no longer a remote outpost; it's where customer experience, cloud... more
 January 28, 2026
January 28, 2026 
 4 min read
4 min read
Private 5G: The Catalyst for Next-Gen Industrial IoT and Factory Automation As Industry 4.0 gains momentum, e... more
 November 20, 2025
November 20, 2025 
 6 min read
6 min read
Why Private 5G Networks are the Backbone of Industry 4.0 Revolution The fourth industrial revolution, Industr... more
 November 20, 2025
November 20, 2025 
 5 min read
5 min read
How a Dedicated Internet Connection Transforms Business Productivity and Uptime In an era where digital opera... more
 November 20, 2025
November 20, 2025 
 5 min read
5 min read
What Makes Airtel's Dedicated Internet a Top Choice for Indian Enterprises? In an era of hybrid work, cloud c... more
 November 20, 2025
November 20, 2025 
 4 min read
4 min read
Leased Line Internet: The Backbone of Successful Hybrid & Remote Work The rapid shift to remote and hybri... more
 November 20, 2025
November 20, 2025 
 7 min read
7 min read
Enterprise Playbook: How to Deploy Your Own Private 5G Network In an era of rapid digital transformation, the... more
 November 20, 2025
November 20, 2025 
 5 min read
5 min read
Choosing the Best Broadband Office Internet Provider in India As businesses increasingly rely on cloud applic... more
 November 18, 2025
November 18, 2025 
 5 min read
5 min read
5 Ways a Dedicated Connection from Leased Line Providers Supercharges Video Conferencing In the era of remote... more
 November 13, 2025
November 13, 2025 
 5 min read
5 min read
Why E-commerce Needs Dedicated Internet Bandwidth for Real-Time Order Processing In the fast-paced world of d... more
 November 13, 2025
November 13, 2025 
 5 min read
5 min read
Thank you for sharing your request with us. We'll get in touch with you soon.
There is already an existing Lead with provided details. Please try after 24 hours.

Something went wrong.
