Mastering 5G Network Management: Strategies for Success
-
April 23, 2024
-
6 min read

The advent of 5G technology promises a seismic shift in the way we connect and communicate. With its ultra-fast speeds, minimal latency, and high capacity, 5G networks are poised to transform various industries, from healthcare to manufacturing and beyond. However, managing and deploying 5G networks effectively present unique challenges, particularly in areas such as security, private network implementation, and overall network management. In this comprehensive guide, we will delve into the essential strategies for mastering 5G network management, providing detailed insights into security measures, 5G private network implementation, and network management best practices.
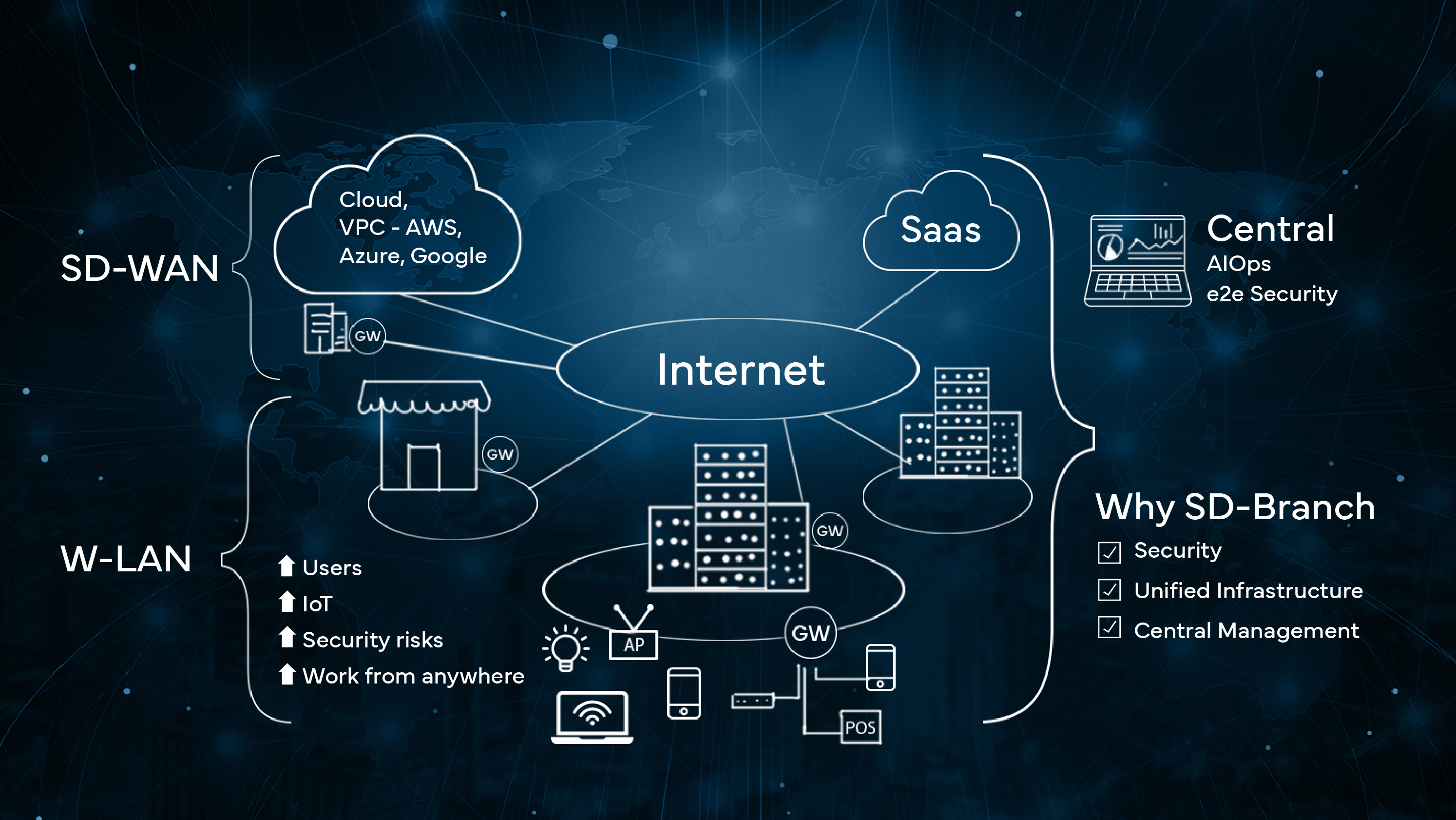
Essential Strategies for Mastering 5G Network Management
Ensuring Robust 5G Network Security
As 5G networks become ubiquitous, ensuring robust security measures is imperative to mitigate potential cyber threats effectively. 5G networks have a distributed nature. It has numerous interconnected devices and sensors, significantly expanding the attack surface for malicious actors. To counter these threats, it’s crucial to implement advanced security protocols such as encryption, authentication, and intrusion detection.
Encryption:
Encryption plays a pivotal role in protecting data transmitted over 5G networks. By encrypting data packets, sensitive information remains unreadable to unauthorized parties, safeguarding the integrity and confidentiality of communication. Advanced encryption algorithms like AES (Advanced Encryption Standard) ensure secure transmission, even in the face of sophisticated cyber attacks.
Authentication:
Implementing robust authentication mechanisms is essential to verify the identity of users and devices accessing the network. By employing techniques like mutual authentication, where both the user and the network authenticate each other, organizations can prevent unauthorized access and protect against impersonation attacks.
Intrusion Detection:
Proactive intrusion detection systems are crucial for identifying and mitigating potential security breaches in real time. By monitoring network traffic and analyzing patterns for anomalous behavior, organizations can detect and respond to security incidents promptly. Intrusion detection systems can also integrate machine learning algorithms to improve accuracy and adaptability to evolving threats.
Moreover, the adoption of network slicing in 5G introduces additional security considerations. Network slicing allows the creation of multiple virtual networks within a single physical infrastructure, tailored to specific applications or user groups. While this enables greater flexibility and customization, it also requires stringent security measures to prevent unauthorized access or interference between slices. Therefore, 5G network operators and enterprises must prioritize the integration of robust security solutions to mitigate the risks associated with network deployments.
You May Like: Steps to Set the Stage for the 5G-Powered Cloud
Implementing Private 5G Networks
The concept of private 5G networks is gaining momentum as organizations seek to harness the benefits of 5G within their premises. Private 5G networks provide dedicated, localized wireless infrastructure tailored to specific business needs, offering reliable connectivity for mission-critical applications and IoT devices.
Spectrum Allocation: Private 5G networks require careful spectrum allocation to ensure optimal performance and interference mitigation. Organizations must acquire the appropriate spectrum licenses and allocate frequencies efficiently to minimize congestion and maximize bandwidth availability.
Network Architecture: Designing the network architecture for private 5G deployments involves configuring base stations, antennas, and network nodes to provide seamless coverage and connectivity. Factors such as coverage area, capacity requirements, and interference levels influence network design decisions, requiring careful planning and optimization.
Interoperability: Ensuring interoperability with existing infrastructure and devices is essential for the seamless integration of private 5G networks into organizational workflows. Compatibility with legacy systems, IoT devices, and third-party applications enables organizations to leverage existing investments while unlocking the benefits of 5G technology.
Additionally, the deployment of private 5G networks necessitates a comprehensive understanding of regulatory requirements and licensing considerations to ensure compliance with local telecommunications regulations. Organizations must navigate legal and regulatory frameworks governing spectrum allocation, frequency bands, and privacy regulations to avoid potential legal pitfalls and ensure successful deployment.
Optimizing 5G Network Management
Effective management of 5G networks is essential for optimizing performance, ensuring reliability, and delivering a seamless user experience. With the proliferation of connected devices and exponential growth in data traffic, network management becomes increasingly complex, necessitating advanced monitoring, analytics, and automation capabilities.
Monitoring and Analytics: Real-time monitoring and analytics tools provide insights into network performance, traffic patterns, and user behavior, enabling organizations to identify bottlenecks, optimize resource allocation, and proactively address issues before they impact user experience. By leveraging data analytics, organizations can gain actionable insights to improve network efficiency, enhance reliability, and deliver superior services to end-users.
Automation: Automation plays a crucial role in streamlining network management operations, reducing manual intervention, and minimizing human errors. By automating routine tasks such as configuration management, provisioning, and troubleshooting, organizations can improve operational efficiency, accelerate response times, and free up valuable resources to focus on strategic initiatives. Automated workflows and orchestration tools enable organizations to adapt to dynamic network conditions, scale resources on demand, and optimize network performance in real-time.
Security Management: Comprehensive security management solutions are essential for protecting 5G networks against evolving cyber threats. By implementing robust security policies, access controls, and threat detection mechanisms, organizations can safeguard critical infrastructure, data assets, and sensitive information from unauthorized access, malicious attacks, and data breaches. Security management platforms provide centralized visibility and control over security policies, enabling organizations to enforce compliance, detect anomalies, and respond to security incidents effectively.
Business Benefits of Effective 5G Network Management
The successful implementation of 5G network management offers significant business benefits across various industries:
Improved Efficiency and Productivity: 5G networks facilitate faster data transmission and reduced latency, enabling real-time communication and decision-making, leading to enhanced operational efficiency and productivity.
Enhanced Customer Experience: Enterprises can deliver immersive experiences to customers through applications like augmented reality and high-definition video streaming, driving satisfaction and loyalty.
Support for Emerging Technologies: 5G networks accelerate the adoption of emerging technologies like edge computing and IoT innovations, empowering enterprises to optimize operations and pioneer new business models.
Challenges in 5G Network Management
Despite the transformative potential of 5G, several challenges must be addressed:
Complex Infrastructure: Managing 5G networks requires sophisticated infrastructure and expertise in network planning, optimization, and maintenance.
Interoperability and Standards: Ensuring seamless interoperability between network elements and devices is critical for 5G network management, requiring standardization efforts to define common interfaces and protocols.
Regulatory Compliance: Navigating regulatory requirements and obtaining spectrum licenses for 5G deployments can be complex, necessitating adherence to local telecommunications regulations and addressing privacy and security concerns.Concl
Also Read: Will 5G Take Over Wi-Fi?
Conclusion
In conclusion, effective management of 5G networks demands a comprehensive approach encompassing robust security measures, private network implementation, and advanced network management capabilities. By prioritizing these strategies, enterprises can navigate the complexities of 5G network management and unlock the full potential of 5G technology. With careful planning and strategic investments, organizations can position themselves to thrive in the era of 5G internet connectivity and drive innovation across their operations.
 Share
Share